What is OCSP stapling?
OCSP stapling is an alternative route to the usual OCSP (Online Certificate Status Protocol) and it is used to check whether or not an SSL/TLS certificate is valid.
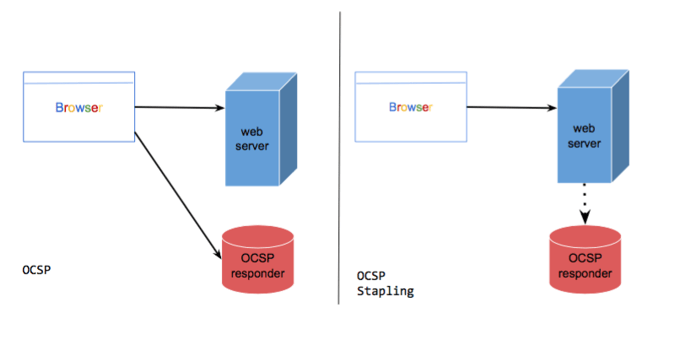
OCSP allows the web server to to determine the status of an SSL/TLS certificate by verifying it with the vendor of the certificate. This improved security comes with some performance penalties: the website loading times are increased since the browser must communicate with both the web server and the vendor.
OCSP stapling addresses some of the issues of the original OCSP implementation, reducing communication times and exchanges between browser, web server and certificate vendor. The web server can download a copy of the vendor’s response and deliver it to the browser during the TLS handshake. In this way the browser can check the validity of a certificate without querying the certificate authority.
OCSP stapling overview:
- A web server, hosting a SSL/TLS website, queries the certificate vendor. The vendor replies with the status of the certificate and a digitally signed timestamp.
- A web browser connects to the server and the server appends (“staples”) the vendor’s timestamp with the certificate during the TLS handshake.
- The browser checks the timestamp; if it is signed by the vendor then it can be trusted.
- Based on the OCSP response the browser can either open the page or show an error message.
Why all this?
Hitch, which is a libenv-based high performance SSL/TLS proxy from Varnish Software (read more here: https://www.varnish-software.com/community/hitch), has support for OCSP stapling.
To configure Hitch to use OCSP stapling you need to specify the pem-file setting in your configuration file:
pem-file = {
cert = "mycert.pem"
ocsp-resp-file = "mycert-ocsp.der"
}Here are three other interesting points about Hitch and OCSP stapling:
- Automated retrieval of OCSP responses from an OCSP responder. This can be set up defining the following line in your Hitch configuration file:
ocsp-dir = “var/lib/hitch-ocsp”
Or via command line with the option: --ocsp-dir=mydir.
If the loaded certificate has both the OCSP responder address and the issuer certificate as part of its chain, Hitch will automatically and asynchronously fetch and refresh OCSP staples.
- Verify the OCSP staple; to achieve this, the option ocsp-verify-staple must be enabled in your configuration file:
ocsp-verify-staple = on
- OCSP stapling of responses loaded from disk or file.
Run this openssl command:
openssl ocsp \
-url https://ocsp.example.com \
-header Host ocsp.example.com \
-no_nonce \
-resp_text \
-issuer issuer.pem \
-cert mycert.pem \
-respout ocspresp.der
It will produce a DER-encoded OCSP response, which can be loaded by Hitch.
The URL of the OCSP responder can be found via:
openssl x509 -ocsp_uri -in mycert.pem -nooutComplete documentation: https://hitch-tls.org
Ready to learn more about security in Varnish Plus? Read our security white paper.



